8 Never Told Benefits of Explainer Videos

Explainer videos are short-animated presentations elucidating a product, service, or idea. Recently, they’ve become integral to modern marketing strategies. While ...
Read more
Digital Footprints: Unraveling the Trail You Leave While Browsing Online

You’re constantly online, leaving a trail of digital footprints. But do you know what they reveal about you? Your habits, ...
Read more
Unveiling the Technical Wonders of eSIM Technology

In the ever-evolving landscape of telecommunications, eSIM (embedded SIM) technology has emerged as a revolutionary force, reshaping the way we ...
Read more
Revolutionizing File Sharing: Unleashing the Potential of “Files Over Miles”

File sharing over the internet has become increasingly important in today’s world of constant technological change. “Files Over Miles” is ...
Read more
IBM 50 partners with Novec and CNBC for innovative tech solutions

What is IBM 50? The ibm 50b novetcnbc, also known as IBM System/360 “the ibm 50b novetcnbc” Model 50, is ...
Read more
Enhancing Business Efficiency Through IT Support in Indianapolis and Managed IT Services

Any company hoping to compete in today’s fast-paced, technologically-driven business market must have access to trustworthy IT support and managed ...
Read more
How Wireless Panic Buttons Increase Safety and Security

In a world of persistent security threats, there is a growing need for tools that can enhance public safety. One ...
Read more
The Importance of Custom MX Graphics

Are you a motocross lover looking to improve your dirt bike’s impression and performance? If so, you’ve come to the ...
Read more
Lindsay Clancy: Shaping the Future of Tech with Innovation and Leadership

With game-changing technologies and forward-thinking leaders, the IT sector is always developing into something new. Lindsay Clancy is one of ...
Read more
Exploring the Enhanced Musical Tapestry: Apple Music Replay 2023
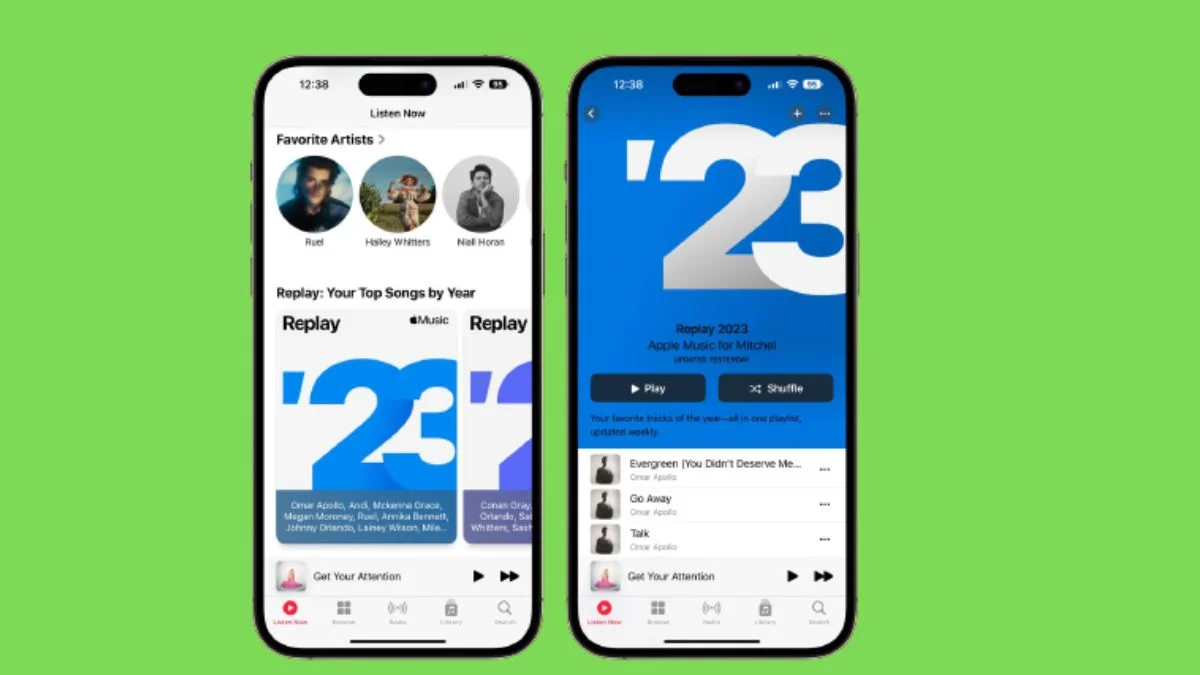
Apple Music has established itself as a leader in the rapidly evolving music streaming industry by introducing ground-breaking new capabilities ...
Read more










